Keyboard Layout Info
A keyboard layout database
Açık Kaynak Rehberleri
Açık kaynak yazılımlar, tıpkı sizin gibi insanlar tarafından geliştiriliyor. Nasıl proje başlatıp büyüteceğinizi öğrenin.
Hardware for Linux or BSD
This is a project to anonymously collect hardware details of Linux-powered computers over the world and help people to collaboratively debug hardware related issues, check for Linux-compatibility and find drivers.
https://linux-hardware.org/ https://forum.linux-hardware.org/?cat=2 https://bsd-hardware.info/
CDemu
“CDemu is a software suite designed to emulate an optical drive and disc (including CD-ROMs and DVD-ROMs) on the Linux operating system.
CDEmu consists of: a kernel module implementing a virtual drive-controller libmirage which is a software library for interpreting optical disc images a daemon which emulates the functionality of an optical drive+disc textmode and GTK clients for controlling the emulator
Optical media emulated by CDemu can be mounted within Linux. Automounting is also allowed.
It is licensed under the terms of the GNU GPL v2 or later.
To learn more about each of the packages comprising the project, please visit their corresponding pages, listed under 'Packages' section on the menu[…]”
https://cdemu.sourceforge.io/about/ https://launchpad.net/~cdemu/+archive/ubuntu/ppa https://wiki.ubuntuusers.de/CDEmu/
Datensicherung unter Ubuntu Gnome 20.04
Es gibt viele Möglichkeiten, wichtige Sicherungskopien zu erstellen. Welche Daten wie gesichert werden, obliegt Ihrer Präferenz. Wir werden hier einige Optionen vorstellen, aber die endgültige Entscheidung obliegt Ihnen. Sie können auch eine Mischung aus mehreren dieser Optionen kombinieren.
Sicherungsrichtlinien
Der Schlüssel zu guten Sicherungskopien liegt darin, dass die Daten automatisiert gesichert, zugänglich, sicher und redundant sind. Alle Sicherungskopie-Lösungen sollten anhand dieser vier Kriterien bewerten lassen:
• Automation: Die Daten werden automatisch gesichert. Manuelle Kopien funktionieren in einigen Fällen gut, aber automatische Datensicherungen stellen sicher, dass Ihre Daten immer aktuell sind und nichts verloren geht. • Zugang: Daten müssen abrufbar und leicht wiederherstellbar sein, falls das Original verloren geht Sicherheit/Datenschutz: Die Daten müssen nur dem Eigentümer zugänglich sein. •Cloud-Lösungen sind praktisch, aber möglicherweise sind zusätzliche Schritte erforderlich, um sicherzustellen, dass die Daten privat sind. •Redundanz Daten müssen sich an mehreren Orten befinden, wenn sich alle Sicherungen an einem Ort befinden. Erhöht sich das Risiko eines Datenverlusts (wenn Ihre Daten beispielsweise in Ihrem Haus auf einem USB-Stick gespeichert werden, es jedoch brennt, können sowohl der Computer als auch die Datensicherung möglicherweise verloren gehen.)
HINWEIS Bewährte Vorgehensweisen zur Vermeidung von Datenverlust bestehen darin, sicherzustellen, dass alle wichtigen Dateien an mindestens drei (3) Orten gesichert werden. Zwei (2) Kopien vor Ort und eine (1) Kopie außerhalb. Diese externe Sicherung kann über eine Cloud-Speicherlösung, ein Laufwerk, das bei einem Verwandten aufbewahrt wird, oder in einem Safe erfolgen.
Benutzerdaten
Benutzerdateien sind die am häufigsten zu sichernden Daten. Dazu gehören Dokumente, Bilder und andere persönliche Dateien. Normalerweise werden diese Dokumente alle in Ihrem Home-Verzeichnis gespeichert (/home/benutzername).
Deja Dup
Déjà Dup aka „Datensicherungen“ist eine beliebtes, unkompliziertes Datensicherungsprogramm. Es kann verwendet werden, um Benutzerdaten lokal, aus der Ferne oder auf einem Cloud-Server zu sichern. Es kann auch so eingerichtet werden, dass es regelmäßig automatisch ausgeführt wird.
Installation
Um Deja Dup zu installieren, suchen Sie in Ubuntu-Software nach Deja Dup oder führen Sie diesen Befehl im Terminal(Strg+alt+t) aus:
sudo apt install deja-dup
Sobald Deja Dup installiert ist, wird es in der Aktivitätenübersicht als „Datensicherungen“ gekennzeichnet.
Auswahl der zu sichernden Daten
Wenn Deja Dup (Datensicherungen) geöffnet ist, können Sie die Ordner auswählen, die Sie speichern oder ignorieren möchten, indem Sie die links aufgelisteten Seiten auswählen. Standardmäßig sichert Deja Dup Ihr gesamtes Home-Verzeichnis, das Ihre Ordner Dokumente, Bilder, Musik und Videos enthält. Es ignoriert Ihren Downloads-Ordner und alle Elemente im Papierkorb. Verwenden Sie die Plus- und Minus-Schaltflächen nach Bedarf, um beide Kategorien zu ändern.

Auswählen eines Speicherorts
Auf der Seite Speicherort können Sie den Ort konfigurieren, an dem Ihre Sicherungskopie gespeichert wird.

Die verfügbaren Optionen sind:
Lokaler Ordner – Sichern der Daten auf einer internen oder externen Festplatte, SSD oder einem USB-Flash-Laufwerk.
Vorteile: Einfach einzurichten, automatisch, zugänglich und sicher. Backups erfolgen in der Regel schnell, da sie eine Direktverbindung verwenden. Nachteile: “Single Point of Failure”( zentraler Schwachpunkt). Wenn der Computer verloren geht oder beide Laufwerke ausfallen, gehen die Daten verloren.
Netzwerkserver- Sichern Sie Daten auf einem anderen Computer oder Speichergerät (NAS) in Ihrem Netzwerk.
Vorteile: Gleiche Vorteile wie bei einer lokalen Sicherungskopie, aber mit weniger „Single Point of Failure“(zentraler Schwachpunkt).Nachteile: Erfordert einige Netzwerkkenntnisse und die Möglichkeit, einen anderen Computer oder ein anderes Speichergerät einzurichten, um die Daten zu speichern. Backups dauern in der Regel aufgrund der langsameren Übertragungsgeschwindigkeiten über das Netzwerk länger (aber immer noch schneller als über das Internet).
Planen regelmäßiger Sicherungskopien
Um die automatische Ausführung von Sicherungskopien zu planen, wählen Sie in der Liste auf der linken Seite Zeitplanung aus und schalten Sie dann den Schalter um, um automatische Sicherungen zu aktivieren. Planen Sie die Sicherung für einen Zeitpunkt, zu dem Sie wissen, dass der Speicherort verfügbar ist (z. B. wenn Sie ein USB-Laufwerk angeschlossen ist). Am häufigsten wird entscheiden, dass Sicherungen über Nacht oder am Wochenende erfolgen.

Wiederherstellen Ihrer Daten
Um Ihre Daten mit Deja Dup wiederherzustellen, wählen Sie die Übersicht und klicken Sie dann auf die Schaltfläche Wiederherstellen... Auf diese Weise können Sie den Speicherort auswählen, der den Deja Dup-Sicherungsordner enthält, und die Daten aus der neuesten Sicherung an ihren ursprünglichen Speicherort kopieren.

Cloud Desktop Clients
Viele Onlinedienste bieten kleine Mengen an kostenlosem Speicherplatz und Desktop- Clients mit automatischer Synchronisierung. Einige Beispiele für Unternehmen, die plattformübergreifenden Cloud-Speicher anbieten, sind:
Tuxedo (basiert auf Nextcloud) Dropbox Mega.nz Box.com (CLI only)
Nextcloud ist eine Open-Source-Cloud-Lösung, die vollständig vom Benutzer gesteuert wird. Der Remote-Server muss manuell eingerichtet werden (oder ein vertrauenswürdiger Drittanbieter könnte bezahlt werden, um den Server einzurichten und zu warten.)
Falls Ihr nicht wisst wie euer Nextcloud mit Deja Dup synchronisiert werden kann. Ihr nutzt die webdav Notation.
Bsp.: davs://beispiel.de/remote.php/dav/files/BENUTZERNAME/
Ihr werdet erneut um eure Zugangsdaten gebeten, ja auch der Benutzername wird erneut abgefragt.
Ihr könnt auch die davs Notation auf dav wechseln und vice versa
Weiterführende Informationen
https://askubuntu.com/questions/1274236/backups-deja-dup-is-missing-nextcloud-option-in-20-04-lts
Daten manuell mit dem Dateibrowser(z.B. Nautilus) kopieren
Wenn ein externes Laufwerk angeschlossen ist, können Daten manuell auf ein externes Laufwerk kopiert werden. Verwenden Sie den Dateibrowser, um Daten vom internen Laufwerk auf das externe Laufwerk zu kopieren. Vorteile: Einfaches und unkompliziertes Kopieren von Daten von einem Ort zum anderen. Nachteile: Da der Prozess manuell ist, können Aktualisierungen und Änderungen an den Daten im Laufe der Zeit übersehen werden. Keine geografische Redundanz.
Terminal (für fortgeschrittene Nutzer. Falls jemand Berührungsängste hat)
In bestimmten Situationen haben Sie möglicherweise nur Zugriff auf eine Befehlszeilenschnittstelle. Das rsync-Befehlszeilenprogramm überprüft die Datenintegrität und vermeidet das erneute Kopieren von Dateien, die bereits gesichert wurden.Ein Beispiel für den rsync-Befehl wäre: rsync -a ~/ AUSGABEPFAD ...wobei rsync -a anweist,die Sicherung als Archiv auszugeben, ~/ sich auf Ihr Home- Verzeichnis als Quellverzeichnis bezieht und AUSGABEPFAD durch das Verzeichnis Ihrer externen Festplatte oder Ihres remote gemounteten Servers ersetzt werden sollte.
Wenn Sie über einen Webbrowser auf Ihre E-Mails zugreifen, ist eine manuelle Sicherung wahrscheinlich nicht erforderlich, da die Daten immer auf einem Remote-Computer gespeichert werden. Wenn Sie einen lokalen Client wie Thunderbird oder Evolution verwenden, können die Daten an mehreren Orten (wie dem E-Mail-Server und anderen Client-Geräten) oder nur an einem Ort gespeichert werden. Bei Verwendung des IMAP- Protokolls werden die Daten zwischen allen Clients synchronisiert; bei Verwendung des POP-Protokolls werden die Daten nur auf dem Client gespeichert, auf dem die E-Mail eingesehen wurde.
Web Browser
Vorteile: Alle Daten befinden sich immer auf einem Remote-Server.
Nachteile: Erfordert Internetzugang. E-Mail-Anbieter haben möglicherweise Zugriff auf Daten.
IMAP
Vorteile: Die Daten werden zwischen dem Remote-Server und lokalen Geräten synchronisiert. Kein „Single Point of Failure“(zentraler Schwachpunkt). Nachteile: Erfordert Internetzugang. E-Mail-Anbieter haben möglicherweise Zugriff auf Daten.
POP/POP3
Vorteile: Daten sind sicherer, da sie sich immer nur an einem Ort befinden.
Nachteile: Der Client, der Daten speichert, ist ein „Single Point of Failure“(zentraler Schwachpunkt).
Benutzerkonfigurationsdateien
Die meisten Benutzerkonfigurationsdateien werden im Home-Ordner gespeichert. Diese können im Allgemeinen wie jede andere Datei kopiert und gespeichert werden, aber das Wiederherstellen dieser Dateien funktioniert möglicherweise nicht immer. Gelegentlich ändern Programme, wie, wo oder in welchem Format ihre Konfigurationsdateien gespeichert werden. Dies bedeutet, dass sie nicht immer wiederherstellbar sind oder möglicherweise nicht wie vorgesehen funktionieren. Es wird empfohlen, diese bei Bedarfzu sichern, aber denken Sie daran, dass sie möglicherweise nicht richtig wiederhergestellt werden.
Die meisten Benutzerkonfigurationsdateien befinden sich im Home-Verzeichnis und
beginnen mit einem Punkt (zB .config Verzeichnis.)
Programme
Da Programme leicht online verfügbar sind (normalerweise über die Software- Repositorys), empfehlen wir nicht, sie zu sichern. Sie sind über das Dateisystem verteilt und lassen sich nur schwer richtig wiederherstellen. Zum Sichern von Programmen empfehlen wir, eine Liste mit Paketnamen für die von Ihnen verwendeten Programme zu führen, damit sie mit einem einzigen Paketmanagerbefehl wie folgt neu installiert werden können:
sudo apt install gnome-tweak-tool mousepad aptitude thunar
Programmkonfigurationsdateien
Systemweite Programmkonfigurationsdateien können an vielen Stellen des Betriebssystems gefunden werden. Der häufigste Ort ist das /etc Verzeichnis. Die meisten davon können auf dieselbe Weise wie Benutzerkonfigurationsdateien gesichert werden, mit der gleichen Einschränkung bezüglich Änderungen des Konfigurationsformats beim Wiederherstellen dieser Dateien. (Sofern Sie die systemweiten Konfigurationsdateien nicht manuell geändert haben, werden die meisten Konfigurationen normalerweise pro Benutzer im Home-Verzeichnis gespeichert.)
Erstellen und Wiederherstellen von Festplatten-Images mit der Laufwerke-App
Ubuntu wird mit einem Dienstprogramm zur Datenträgerverwaltung namens GNOME Discs(Laufwerke , vormals Palimpsest) geliefert. Sie finden es in Ihrer App-Liste.

Nach dem Öffnen sehen Sie auf der linken Seite eine Liste aller Festplatten, die an Ihren Computer angeschlossen sind. Wählen Sie die Festplatte aus, die Sie sichern oder wiederherstellen möchten, und klicken Sie darauf.

Sobald Sie eine Festplatte auswählen, wird eine Schaltfläche „Laufwerkseinstellungen“ in der oberen rechten Ecke des App-Fensters angezeigt. Wenn Sie darauf drücken, wird ein Dropdown-Menü angezeigt, in dem Sie die gewünschte Option auswählen können – ein Laufwerksabbild erstellen oder -wiederherstellen.
Laufwerksabbild erstellen

Wenn Sie im oben erwähnten Dropdown-Menü auf “Laufwerksabbild erstellen” klicken, wird ein Popup-Fenster angezeigt, in dem Sie die Möglichkeit haben, das von Ihnen erstellte Laufwerksabbild zu benennen und auszuwählen, wo es abgelegt werden soll.
HINWEIS Dass Erstellen eines vollständigen Laufwerksabbilds nur verfügbar ist, wenn von einem live USB-Stick gebootet wird. Alternativ besteht auch die Möglichkeit, ein Multi bootfähigen Ventoy-Stick zu erstellen. Sie können keine Änderungen an einer internen Festplatte oder Partition vornehmen, von der Sie booten. Nachdem Sie auf „Erstellung starten“ geklickt haben, werden Sie möglicherweise nach Ihrem Passwort gefragt. Als Nächstes beginnt Laufwerke mit der Erstellung Ihres Abbilds. Ein Fortschrittsbalken wird angezeigt. Sie können die Erstellung des Bildes jederzeit abbrechen, indem Sie auf das Papierkorb-Symbol rechts neben dem Fortschrittsbalken klicken.
HINWEIS Der Speicherort, an dem Sie die .img Datei speichern, muss entweder gleich groß oder größer sein (d. h. 1 TB benötigt 1 TB oder mehr).Wenn der Vorgang angeschlossen ist, haben Sie ein Laufwerksabbild im .img-Format. Die Datei hat den von Ihnen gewählten Namen und wird in dem von Ihnen ausgewählten Ordner gespeichert.
Laufwerksabbild Wiederherstellen
ACHTUNG: Beim Wiederherstellen eines Laufwerkabbilds auf einem Laufwerk wird der aktuelle Inhalt des ausgewählten Laufwerks oder der ausgewählten Partition überschrieben. Dies führt wiederum zu einem vollständigen Datenverlust. Stellen Sie Laufwerksabbilder nur auf Laufwerken wieder her, die bereits gesichert wurden oder auf denen wo dies keine Relevanz hat.
Wenn Sie im oben erwähnten Dropdown-Menü auf „Laufwerksabbild wiederherstellen“ klicken, erscheint ein Pop-up mit einer Schaltfläche zur Auswahl des Abbilds, das Sie wiederherstellen möchten(links).
Nachdem Sie auf “Wiederherstellung starten” geklickt haben, werden Sie nach einer Bestätigung und möglicherweise nach einem Benutzerkennwort gefragt. Danach beginnt der Prozess der Wiederherstellung eines Disk-Images auf Ihrer Festplatte und zeigt Ihnen den Fortschritt der Wiederherstellung an. Sie können jederzeit abbrechen, indem Sie auf das Papierkorbsymbol rechts neben der Fortschrittsleiste klicken.
HINWEIS Selbst wenn Sie die Taste zum Abbrechen drücken, wurde Ihre ausgewählte Festplatte bereits überschrieben, um Platz für das Wiederherstellungsabbild zu erzeugen.
Wenn der Vorgang abgeschlossen wurde, haben Sie Ihr Laufwerksabbild und Ihre Daten auf der von Ihnen ausgewählten Festplatte.
Mammon
Mehr Zukunft wagen? Hahaha… Ich, ich würde lachen und nicht klagen.
Die Zukunft ist nicht begraben in den vergangenen Tagen, das würde ich euch gerne glauben machen.
Grün des Dollars in den Augen der Beraubten, die einst glaubten, sie würden dazu zählen.
Doch die Rechnung geht nicht auf, denn nicht jeder kann Millionär werden. Außer, er erbt reich oder Fortuna schenkt ihm Reichtum.
The winner takes it all – Jeff Bezos, Musk, Buffet gefällt diese Wendung. Ihre Kassen werden durch Schlupflöcher prall. Schaut euch um, dies geschieht schneller als der Schall.
Und viele, viel mehr werden entbehren. Dieser Tragikomödie kann man sich kaum entziehen,
Gaia erhebt sich und mit einem Donner wirbelt Sie die Richter, Schlichter und Henker in die Luft.
Denn die stolze Menschenbrut, Gottes Ebenbild, tut gut daran, sich in Enthaltsamkeit zu üben. Wie steht es bei Goethe geschrieben? “Entbehren sollst du! Sollst entbehren!” Und sollte sich nicht weiter mit Luftschlössern den Blick trüben.
Die, die glaubten, sie würden einst dazu gehören, werden sich gewiss nicht daran stören, sich weiter der Torheit zu widersetzen, die sie einst glaubten.
Die Törichten wissen es nicht und können es nicht fassen. Sie lieben das, was sie eigentlich hassen sollten.
Aber lasst sie nur…
Sie haben es vermasselt und werden es nicht verstehen, bis es auf sie prasselt.
Der grimmige Groll der Gebeutelten, erfüllt von wehleidigem, schmerzvollem Heulen.
Dieses Narrengeschrei werden wir mehr vernehmen, denn es wird davon noch zuhauf geben.
Die Demokratie kann nur im Wohlstand überleben. Plutokraten suchen dies nicht und verwehren es.
Der Nachtalb
Meine Muse ist nicht Mahr In Dunkelheit Sie gebar.
Den Schein eines Fiebertraums
Entzweit hatten wir uns
Während der Umtrunke Des bitteren Wermuts
Charybdis und der Skylla gleich umschlungen in dieser dunklen Finsternis
Sank ich umrankt in den Abyssos Welcher mir gleicht dem Limbus
Mich in dem transzendent Wahn hinein stoß
Auf ewig die Wiederholung Auf ewig dasselbe spiel Auf ewig die Umnachtung in die ich viel.
Vergebens der kalten Theatralik des Lebens, das Schicksal Zu entfliehen
Bleibe ich liegend, bleibe ich stehen
Und blicke ins Nichts.
Gespenster aus alter Zeit machten sich auf. Plump und dumm. Standen sie aus Ihren Gräbern auf.
Und legten ein Zeugnis ab.
Sie waren nie fort. Sie waren immer vor Ort.
Sie versteckten Sie hinter den biederen wieder.
Wir sollten uns weigern, nie wieder!
Werden wir den Boden verlassen Für diejenigen, die entzweiten und hassen.
Um auf der Bühne Ihr Spiel zu treiben Und jeder tut dies seinen.
Und dennoch mimen die stummen Kontorsionisten ihresgleichen
Der Drang laut aufzuschreien Die bösen geister zu vertreiben
Den unsere Negation den Weg bereitete Erscheint mir nichts als Verneinung des seins.
Display GIFs in your terminal
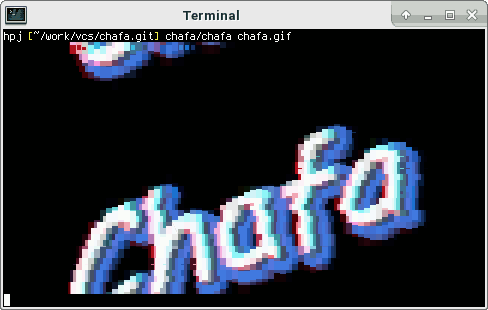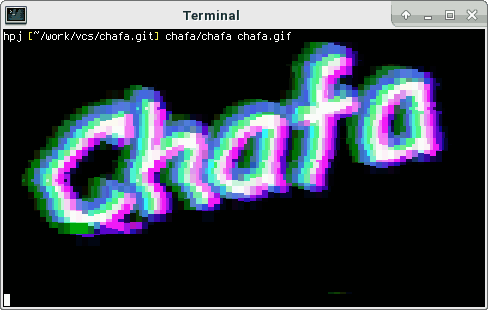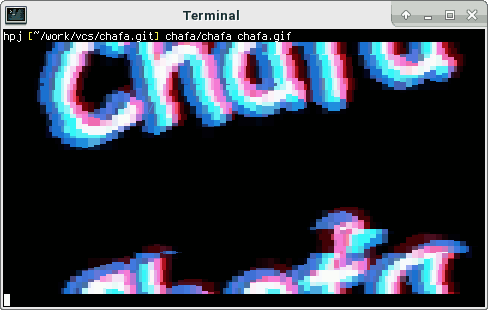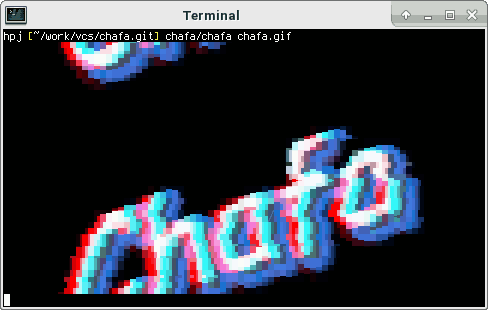
Open your terminal on most distributions this can be achieved via this three key combinations, CTRL+ALT+t
sudo apt install -y chafa
then type
chafa nameOfTheGIF.gif
Magic!
Further reading:

